Seasoned security experts leverage the complete ArmorPoint security tool stack to proactively mitigate and automatically remediate advanced threats across network, cloud, and endpoint attack vectors.

Unparalleled Protection Meets Expert Vigilance
Simplify your security operations and steer clear of threats with unmatched expertise. Effortlessly consolidate alerts, bridge in-house expertise gaps, and gain a panoramic view of your security landscape with ArmorPoint’s Managed SOC.
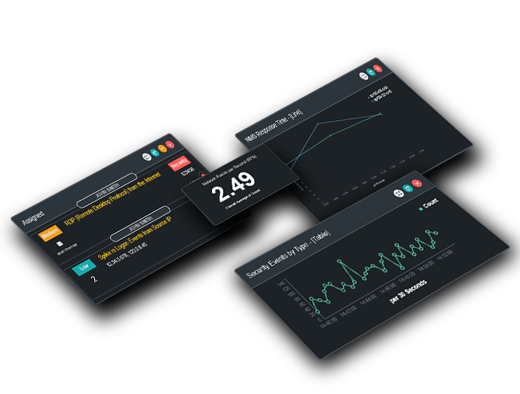
Gain Unrestricted Visibility
Make your organization responsive to cyber risk. ArmorPoint’s Managed SOC solutions ensure you’re safeguarded today and prepared for the challenges of tomorrow.

Scalable SecOps
It’s more than just prevention; it’s about building cyber resilience that supports business growth.
- Fill the tactical gaps in key people, processes, and technology
- Allocate resources based on business priorities
- Keep your team focused on larger strategic initiatives

24×7 Vigilant Monitoring
True threat detection, investigation, and response that goes beyond advanced technology.
- Ensure round-the-clock network protection
- Extend your workforce with a U.S.-based team of seasoned cybersecurity professionals
- Use our team to relentlessly hunt, detect, investigate, triage, and remediate malicious activity 24×7
Unify your Security Stack
Say goodbye to duplicate alerts and a disparate security stack.
- Utilize ArmorPoint’s cloud-based SIEM for event log ingestion from network devices, cloud environments, endpoints, and existing security tools
- Enhance visibility and simplify security management

Managed SOC Packages
Pair the ArmorPoint cloud-based SIEM, ArmorPoint Agent, and expert managed SOC services with your existing EDR tool to streamline SecOps.
ArmorPoint SOC analysts go beyond traditional endpoint detection and response with an AI-powered next-gen antivirus, offering a proactive defense that anticipates risks and automatically remediates valid threats.
Support Your SOC with Managed Risk and Strategy
Combining the strengths of Managed Risk, Managed Strategy, and Managed SOC doesn’t merely boost your security program — it transforms it entirely. Allow Managed SOC to vigilantly shield you from immediate threats, as Managed Risk zeroes in and bolsters potential vulnerabilities, all while Managed Strategy paves a path towards future-proof cybersecurity.
Managed Risk
Transform vulnerabilities into valuable insights for intelligent decision-making.
Comprehensive Risk Assessment
Understand your security landscape with thorough evaluations, highlighting vulnerabilities and points of improvement.

Adaptive Risk Framework
As your business evolves, so does our approach. We adapt to ensure you’re always one step ahead of potential threats.
Customized Training Modules
Elevate your team’s cybersecurity knowledge with our tailored training programs, ensuring they have the knowledge and skills needed to be the first line of defense against potential cyber threats.

Managed Strategy
Fortify your business’s future with holistic and strategic security planning and execution.
Cybersecurity Roadmapping
Craft your secure path forward, leveraging our custom roadmaps that encompass both current capabilities and future goals, guaranteeing an adaptable defense blueprint.

Expert Guidance
Benefit from the expertise of seasoned cybersecurity professionals, guiding you through every twist and turn of doing business in the modern threat landscape.
Seamless System Integration
Experience smooth transitions and enhanced functionality with ArmorPoint’s Security Solutions, expertly designed to seamlessly integrate with your existing operations.






